This is an old revision of the document!
Lab extra FTD
Story
Topology
Exercises
Exercise 1 - MITM decryption in depth [4p]
Remember that last time we created an SSL decryption rule based on an already existing CA certificate generated on the machine. In order for clients to not be affected by this inspection, we required to import the certificate on browser's trust store (Mozilla in our case). There are 2 ways of providing a custom certificate:
- generate via WebUI (you are just required to add a name and complete the fields of distinguished name or DN - the private key is generated directly by the firewall)
- generate using openssl package (you will need to generate the certificate in pem format and the private key)
a) Generate cert on WebUI [2p]
This time we want to create a new one (from Objects > Certificates), with a different CN (you can use ‘student’) on DN. The rest of the fields (like organization), can be left blank here.
You need to delete the old SSL decryption rules (added on the last lab for TLS obsolete blocking and decryption) and add the new certificate generated above. Firstly, we do not want to inspect sensitive data (like medical or financial URL categories), then to decrypt and analyze https traffic. Add these 2 rules and deploy.
You need to also import the CA certificate (again using privnote) on the trust store from client1's machine (hint: update-ca-certificates).
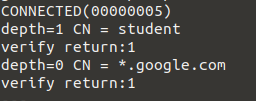
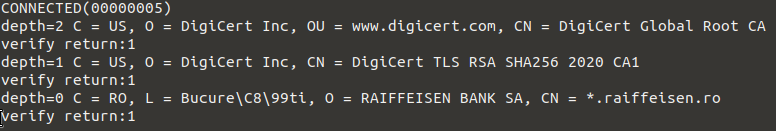
Then, check using openssl s_client (hint: –showcerts) if the traffic is decrypted or not. Check firstly google.com or facebook.com and see if the CA certificate used in key chain is the one configured above and then check with brd.ro - finance and reginamaria.ro - health (or identify new ones using Talos).
Example 1 - checking google.com (custom cert should be used):
See the CN of the first certificate, the continuing with the server's one.
Example 2 - checking raiffeisen.ro (original cert path should not be affected - you should see CAs and sub CAs for other websites like DigiCert):
b) Generate cert using openssl [2p]
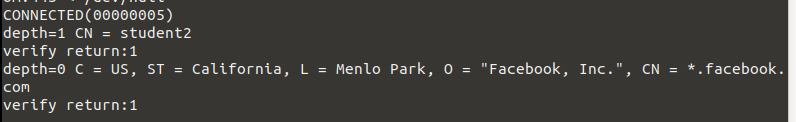
Using openssl client on the eve-ng machine generate a new certificate in pem format with just the subject 'student2' in the DN, with 365 days of availability, private key with 4096b, and with no encryption of private key (do not protect it).
Then, add this second cert and the corresponding private key to FTD's trust store (Objects > Certificates > Add Internal CA > upload cert and key). Upload the CA to the second client (kali), add to trust store and update it. Also, change the CA from SSL decryption policies and deploy.
Check again the 2 scenarios (with google and raiffeisen or any other sites).
Example 3:
Exercise 2 - Security intelligence [3p]
Talos is keeping an internal database of feeds that represents categories of IPs and URLs that are maintained by Cisco. We can block before inspecting traffic using access rules, the IPs or URLs that are retrieved from Talos feeds or directly added by the sysadmin (can be internal IPs that I want to block for some clients or the endpoints that need to be blocked).
Firstly, we need to configure the Security Intelligence Feeds (from Device > Updates):
- leave recurring for 1 hour (the lists are pulled from server and updated on the local FTD without a deployment)
- press 'update from cloud' to get the lists from the cloud for the first time
a) Security intelligence only
Then, blacklist the URL category cryptomining (or any other category for which you can find websites to test later) and leave only the access control rules: allow any from inside and inside2 to outside. Check if the traffic to binance.com is blocked.
Example binance.com - on Talos we can see that this website is added to BLOCK LISTS with CLASSIFICATION Cryptomining.
Test also with another website, like coinmarketcap.com. Is it blocked? Why/why not?
b) Add an access rule
The purpose of this exercise is to understand how we must be very sure about the configuration when chaining different policy types.
Create a new URL object for twitter.com and add it to 'Do not block (Permit)', then create also a new access rule to deny access to URL category 'Social Networking' from inside/inside2 to outside.
Try to access from client1/client2 this website. Does it work?
Exercise 3 - Teamviewer not allowed [3p]
We decided to block teamviewer application on our local networks using a new access rule. Moreover, using the syslog server configured last time (see here the exercise if you did not resolve it) we will send to the server (Linux Router VM) the connection logs when an user tries to access the website/application.
In the same time, we need a way of real time analysis of this logs (the infosec team from the company might want to see which employees are not behaving correctly and may enforce other rules for them).
After deployment, try to access the website. The access should be blocked. Instead of creating a daemon that is inspecting the logs in real time, you can use:
# configure here you access rule name (mine was named block_teamviewer) access_rule_name='block_teamviewer' grep "AccessControlRuleName: $access_rule_name" /var/log/syslog-ng/logs.txt | tail -n 1
to extract the latest entry in the logs file.
Then, install the mailutils in order to send an email for generating an alert - you can use your personal email address here. Send the email and check the spam folder:
mail -s "Alert teamviewer" $your_email_address <<< $(grep "AccessControlRuleName: $access_rule_name" /var/log/syslog-ng/logs.txt | tail -n 1)
In a real life scenario, we will need to analyze the logs file, parse each log, and generate an alert based on some fields (like the source user IP, website accessed, the time of accessing etc.).