This is an old revision of the document!
Laboratorul 09. GRE și IPsec
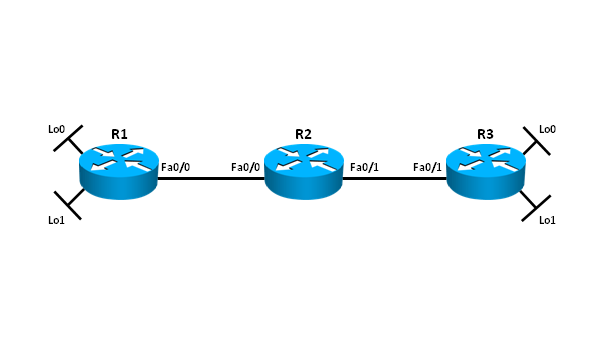
Topologie
Cerințe
Setup
Exerciții
IPSec (5p)
Follow the next steps so that traffic between R1 Loopback0 and R3 Loopback0 is encrypted using IPSec.
ISAKMP
Configure the following ISAKMP policy on both R1 and R3
- authentication: pre-shared keys
- encryption: aes 256
- hashing: sha1
- diffie-hellman group: 2
- lifetime: 3600
The syntax for configuring the policy is the following:
R(config)#crypto isakmp policy <policy_number> R(config-isakmp)#authentication <pre-share | rsa-encr | rsa-sig> R(config-isakmp)#encryption <des | 3des | aes> <key-length> R(config-isakmp)#hash <md5 | sha> R(config-isakmp)#group <diffie_hellman_group_number> R(config-isakmp)#lifetime <lifetime_in_seconds>
Configure “srs!@#” as a pre-shared key on both R1 and R3. The pre-shared key is configured using the crypto isakmp key command:
R(config)#crypto isakmp key <key_index> <key_string> address <peer_address>
IPSec
Configure the following transform set on both R1 and R3:
- Tag (name of the transform set): TS_SRS
- Transform set: esp-aes 256 esp-sha-hmac
- Mode: transport
The commands for configuring a transform-set are the following:
R(config)#crypto ipsec transform-set <transform_set_name> <tranform_set_parameters> R(config-trans)#mode < transport | tunnel>
Construct an access-list that will match the traffic that you want to encrypt.
- The access-list will have to define both the source and the destination of the traffic.
- An access-list must be defined on both R1 and R3.
- Watch out for the fact that the 2 ACLs must mirror each other.
- The access-list can match all IP traffic
Create a crypto-map called TUNNEL_MAP on both R1 and R3.
- The crypto map must match the ACL that you used to define interesting traffic.
- The crypto map must set the remote peer for the tunnel. The remote peer is going to be the IP address of the outgoing Ethernet interface of each router.
- The crypto map must set the transform set to “TS_SRS”
The steps for configuring the crypto-map are the following:
R(config)#crypto map <name> <sequence_no> ipsec-isakmp R(config-crypto-map)#set peer <peer_IP> R(config-crypto-map)#match address <acl_no | acl_name> R(config-crypto-map)#set transform-set <transform_set_name>
Apply the crypto map on interface F0/0 of R1 and F0/1 of R3 using the following command:
R(config-if)#crypto map <crypto_map_name>
Packet Capture
Verify that the traffic is encrypted.
- Use the
capture R2 F0/0 tunnel.capcommand in the dynagen console to start a capture on R2’s F0/0 interface - Generate traffic between loopback interfaces.
- Stop the capture using the
no capture R2 F0/0command in the dynagen console. - Open the tunnel.cap file with Wireshark.