This is an old revision of the document!
Lab06. Data exfiltration
Objectives
- Basic usage of the netcat tool
- Basic usage of the ssh tool
- Data exfiltration through DNS, HTTP, ICMP and UDP
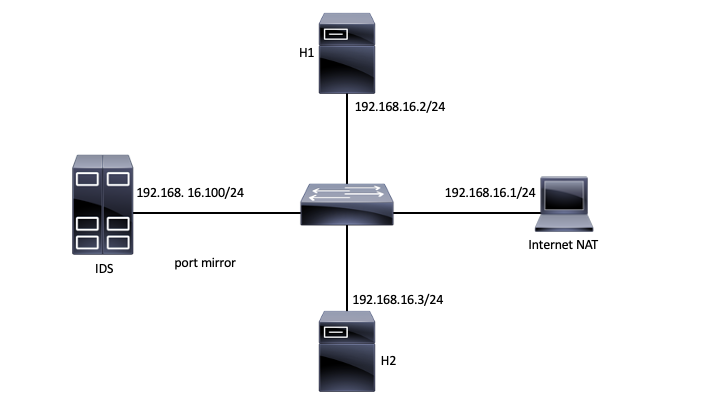
Topology
Tasks
01. [5p] Virtual machine setup
First, make sure that your virtual machine is updated (run the provided update.sh script, or create one).
root@cdci:/# cat update.sh #!/bin/bash # (c) Mihai Chiroiu - CDCI git clone -b labs --single-branch https://github.com/mihai-chiroiu/cdci.git git config user.email "student@upb.ro"
Next, in one terminal start the provided Mininet topology.
root@cdci:/# cd cdci/lab06 root@cdci:/# /usr/bin/python3 topology.py
If there are any problems with starting the topology (if all is good you should see the Mininet prompt ”>”) use the given cleanup script and try to restart the topology.
02. [5p] Internet connectivity
Before you begin, make sure that you have Internet connectivity on all two nodes. R1 should be the gateway. Write down the IP addresses of all the nodes. Use the provided scripts to access the nodes.
root@ip-172-30-0-165:/# ./h1.sh root@h1:/# root@ip-172-30-0-165:/# ./h2.sh root@h2:/# root@ip-172-30-0-165:/# ./ids.sh root@IDS:/#
03. [15p] Plain text exfiltration
Netcat, also known as the 'TCP/IP Swiss Army Knife,' can be used to send data between two hosts. Create a client/server connection over port 8080. By default, the data send from the client will be printed on the server.
The switch in the topology is configured to mirror all traffic to IDS. Use this feature to save the traffic in a PCAP file using 'tcpdump'. Use Netcat to grant the client shell access on the server (hint: '-c' param on the server side).
Download the previously saved PCAP file to your local computer and analyse it using Wireshark. Use the “Follow TCP stream” option from Wireshark to observe the traffic flow between the two hosts.
./copy_from_node.sh IDS /root/traffic.pcap /home/ubuntu/
04. [10p] HTTP exfiltration
While Netcat is a good tool, the traffic that it sends can be easily removed by any Deep Packet Inspection solutions because it is a simple DATA over TCP connection. Now, use the httptunnel (hts & htc) suite to create a HTTP tunnel between the two nodes. Use this tunnel to establish a client/server connection and exfiltrate data (similar to the previous exercise).
To view the traffic you can use tcpdump on the IDS (to view it locally or to transfer it to your computer and open it with Wireshark).
05. [15p] SSH exfiltration
As seen, the previous solutions send data in clear text. Create an ssh tunnel and use it to exfiltrate data via a similar client/server Netcat architecture. For this, you have to use one node as an SSH server and the second one as a client. Use the following configuration on the SSH Server
root@h2:/# vim /etc/ssh/sshd_config PasswordAuthentication yes PermitRootLogin yes root@h2:/# service ssh restart root@h2:/# netstat -nltp Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 198/sshd
To view the traffic you can use tcpdump on the IDS (to view it locally or to transfer it to your computer and open it with Wireshark).
06. [20p] ICMP exfiltration
Another protocol that can be used to exfiltrate data is ICMP. You can use the ptunnel application and tunnel the Netcat client/server connection over ICMP.
To view the traffic you can use tcpdump on the IDS (to view it locally or to transfer it to your computer and open it with Wireshark). For this exercise we strongly encourage you to view the data in Wireshark.
07. [20p] DNS exfiltration
To view the traffic you can use tcpdump on the IDS (to view it locally or to transfer it to your computer and open it with Wireshark).