This is an old revision of the document!
Laboratorul TODO - PKI and TLS
Public Key Infrastructure
In cryptography, a PKI is an arrangement that binds public keys with respective identities of entities (like people and organizations). The binding is established through a process of registration and issuance of certificates at and by a certificate authority (CA).
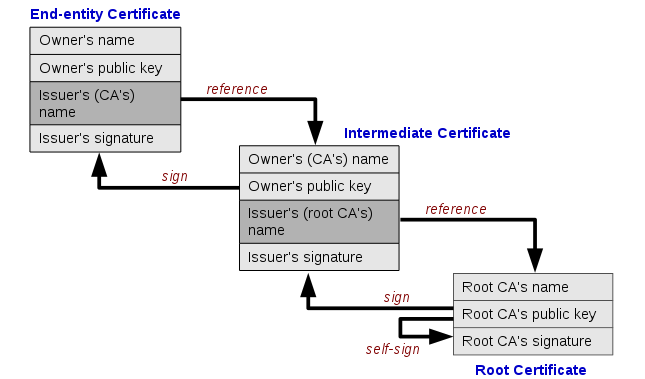
PKI is a system for the creation, storage, and distribution of digital certificates which are used to verify that a particular public key belongs to a certain entity. The PKI creates digital certificates which map public keys to entities, securely stores these certificates in a central repository and revokes them if needed. The roles of root certificate, intermediate certificate and end-entity certificate as in the chain of trust can be seen in the picture below:
Task 1: Investigate certficates for ocw.cs.pub.ro
Using your browser's 'View Certificate' functionality, try to find information about the certificate presented by https://ocw.cs.pub.ro. We are interested in:
- issuer
- validity dates
- subject (CN: Common Name)
- public key
Export server and issuer certificates, or download them from here: certificates.tar. We will use openssl command line tool to investigate certificate files.
openssl s_client -showcerts -connect ocw.cs.pub.ro:443
- Display whole certificate
$ openssl x509 -in ocwcspubro.crt -noout -text $ openssl x509 -in TERENASSLCA3.crt -noout -text
- Display certificate attributes
$ openssl x509 -in ocwcspubro.crt -noout -dates $ openssl x509 -in ocwcspubro.crt -noout -issuer $ openssl x509 -in ocwcspubro.crt -noout -subject $ openssl x509 -in ocwcspubro.crt -noout -pubkey
- Using the certificate of the issuer, we can verify server certificate
$ openssl verify -CAfile TERENASSLCA3.crt ocwcspubro.crt
TLS
The Transport Layer Security protocol aims primarily to provide privacy and data integrity between two communicating computer applications. When secured by TLS, connections between a client (e.g., a web browser) and a server (e.g., wikipedia.org) have one or more of the following properties:
- The connection is private because symmetric cryptography is used to encrypt the data transmitted. The keys for this symmetric encryption are based on a shared secret negotiated at the start of the session.
- The identity of the communicating parties can be authenticated using public-key cryptography and digital certificates.
- The connection ensures integrity because each message transmitted includes a message integrity check using a message authentication code.
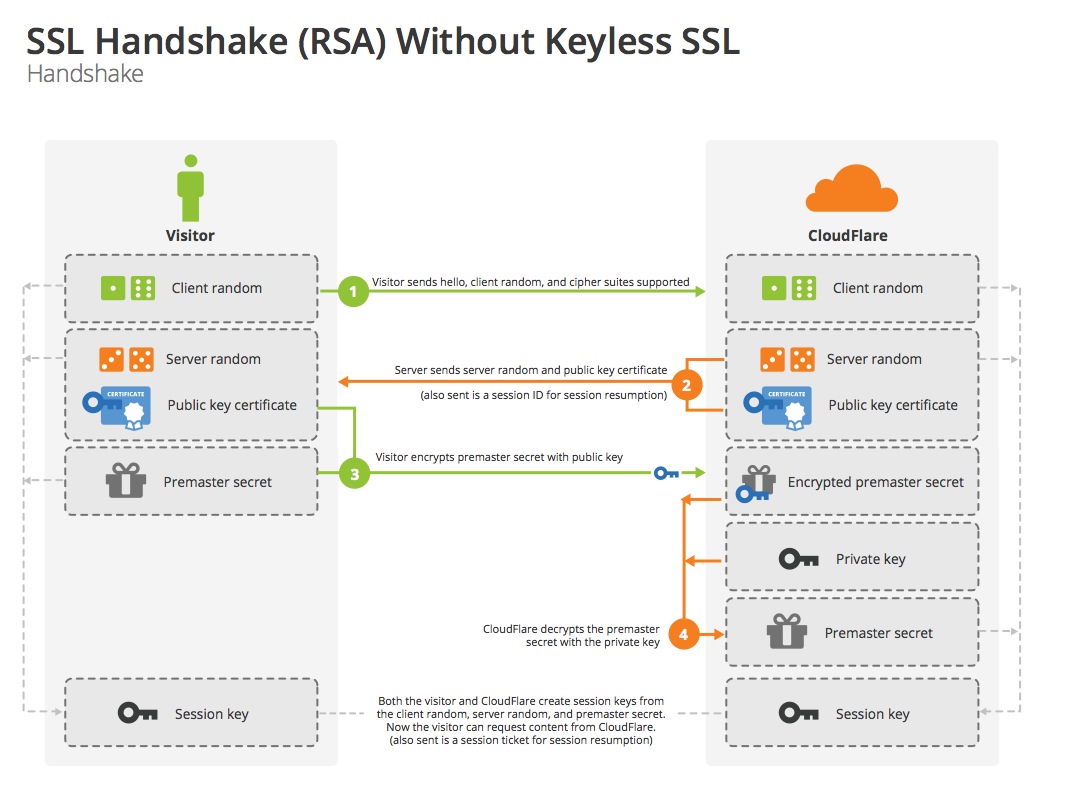
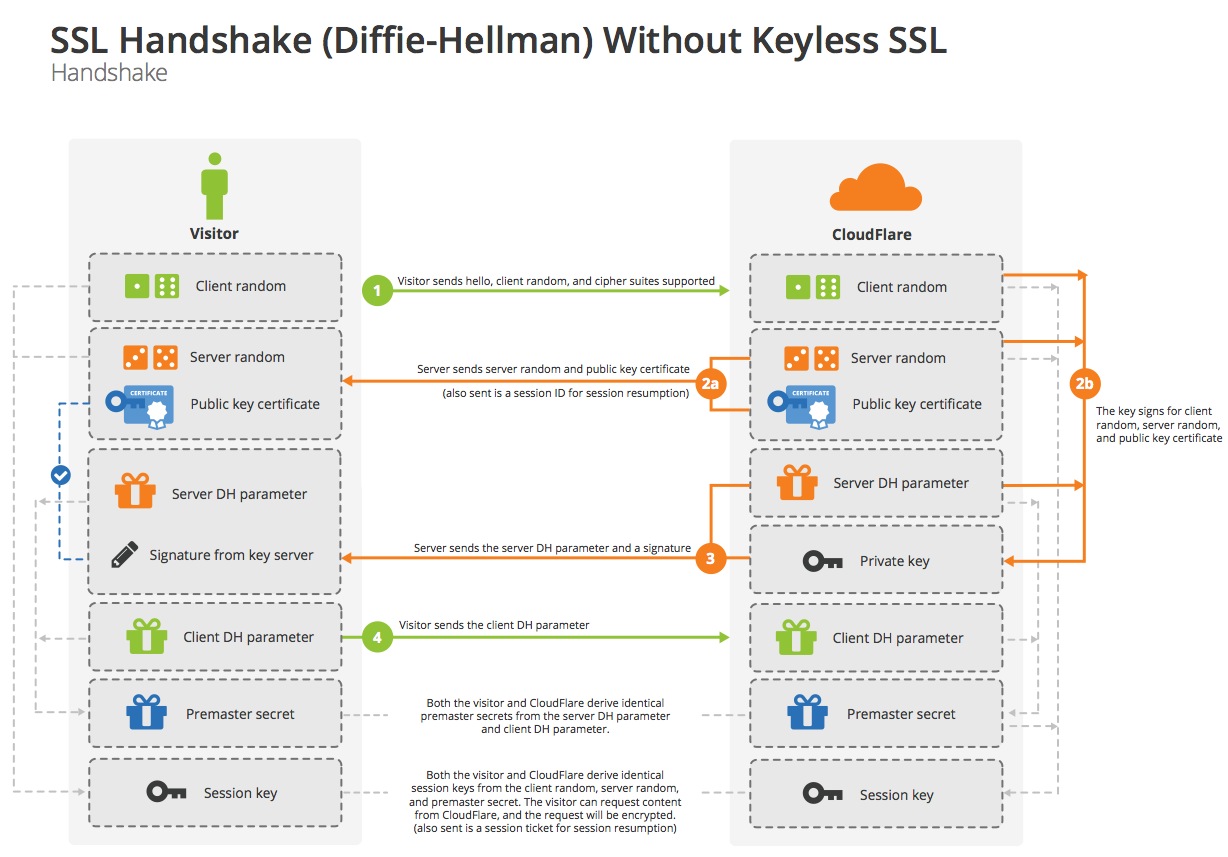
The TLS protocol comprises two layers: the TLS record protocol and the TLS handshake protocol. TLS handshake protocol (both RSA key exchange and Diffie-Hellman key exchange) can be seen in the pictures below:
Task 2: Investigate the TLS handshake protocol
Using Wireshark, investigate the two traffic captures (traffic-captures.tar). In both cases try to find:
- How many ciphersuite does the client support?
- What could be the purpose of Extension: server_name?
- What were the negotiated algorithms?
- What information is sent in cleartext? It is critical? How would a downgrade attack be performed?
Task 3: Create your own CA
- Create directories for CA and for server files
mkdir ca-files server-files
- Create CA private key and certificate (
cd ca-files/)- create CA configuration file
$ cat root-ca.conf [ req ] distinguished_name = req_distinguished_name prompt = no [ req_distinguished_name ] C = RO ST = Bucharest L = Bucharest O = UPB Root CN = UPB Root CA emailAddress = root@root-ca.org
- create CA private key and certificate
openssl req -config root-ca.conf -new -x509 -sha256 -newkey rsa:2048 -nodes -keyout root-ca.key -days 365 -out root-ca.cert
- inspect CA certificate
openssl x509 -in root-ca.cert -text -noout
- Create server private key and Certificate Signing Request (
cd server-files/)- generate server private key
openssl genrsa -out server.key 2048
- create a Certificate Signing Request config file
$ cat server-csr.conf [ req ] distinguished_name = req_distinguished_name prompt = no [ req_distinguished_name ] C = RO ST = Bucharest L = Bucharest O = Applied Cryptography Course CN = applied-cryptography.org emailAddress = office@applied-cryptography.org
- create a Certificate Signing Request
openssl req -config server-csr.conf -new -sha256 -key server.key -out server.csr
- inspect the CSR
openssl req -in server.csr -noout -text
- Submit CSR to be signed by the CA and obtain the server certificate
- move CSR to CA folder
mv server.csr && cd ../ca-files/
- sign the CSR and obtain the server certificate
echo "01" > root-ca.srl openssl x509 -in server.csr -out server.cert -req -CA root-ca.cert -CAkey root-ca.key -days 365 -CAserial root-ca.srl
- inspect and verify server certificate
openssl x509 -in server.cert -text -noout openssl verify -CAfile root-ca.cert server.cert
- move certificate to server files folder
mv server.csr ../server-files/
- Install Apache and activate SSL module
- install Apache server
sudo apt-get update sudo apt-get install apache2
- activate Apache SSL module
sudo a2enmod ssl
- enable the default HTTPS site
sudo a2ensite default-ssl
- point applied-cryptography.org to 127.0.0.1
echo "127.0.0.1 applied-cryptography.org" | sudo tee -a /etc/hosts
- restart server and inspect HTTPS website (https://applied-cryptography.org, notice the error occured)
sudo service apache2 restart
- Configure Apache to use our certificate
- copy certificate and private key
sudo cp server.key /etc/ssl/private/ sudo cp server.cert /etc/ssl/certs/
- install our certificate and private key on the server
sudo vim /etc/apache2/sites-available/default-ssl.conf # update SSLCertificate paths
- restart the server
sudo service apache2 restart
- visit https://applied-cryptography.org, notice the error occured
- install CA certificate in Firefox
navigate to Menu > Preferences > Advanced > Certificates > View Certificates click Import and choose root-ca.cert
- revisit https://applied-cryptography.org (you probably need to launch an incognito window)