This is an old revision of the document!
Lab 05 - PKI and TLS
Task 1: Implement DH + AES-GCM encryption
Implement DH + AES-GCM encryption starting from the code from previous lab (see bonus 2).
Use the secret key to encrypt some data and check that the other party can decrypt it. You can use the code available here for AES-GCM.
Public Key Infrastructure
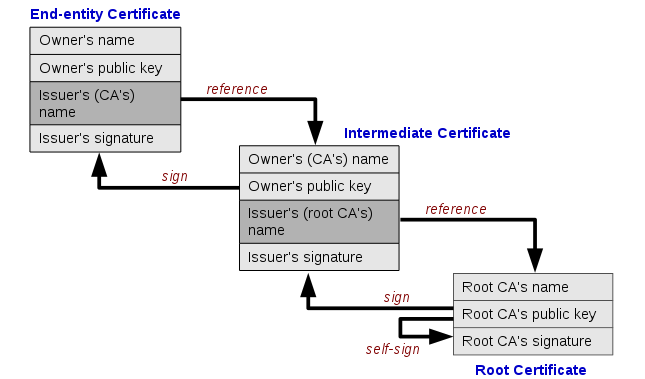
In cryptography, a PKI is an arrangement that binds public keys with respective identities of entities (like people and organizations). The binding is established through a process of registration and issuance of certificates at and by a certificate authority (CA).
PKI is a system for the creation, storage, and distribution of digital certificates which are used to verify that a particular public key belongs to a certain entity. The PKI creates digital certificates which map public keys to entities, securely stores these certificates in a central repository and revokes them if needed. The roles of root certificate, intermediate certificate and end-entity certificate as in the chain of trust can be seen in the picture below:
Task 2: Investigate certficates for ocw.cs.pub.ro
Using your browser's 'View Certificate' functionality, try to find information about the certificate presented by https://ocw.cs.pub.ro. We are interested in:
- issuer
- validity dates
- subject (CN: Common Name)
- public key
Export server and issuer certificates, or download them from here: certificates.tar. We will use openssl command line tool to investigate certificate files.
openssl s_client -showcerts -connect ocw.cs.pub.ro:443
- Display whole certificate
$ openssl x509 -in ocwcspubro.crt -noout -text $ openssl x509 -in TERENASSLCA3.crt -noout -text
- Display certificate attributes
$ openssl x509 -in ocwcspubro.crt -noout -dates $ openssl x509 -in ocwcspubro.crt -noout -issuer $ openssl x509 -in ocwcspubro.crt -noout -subject $ openssl x509 -in ocwcspubro.crt -noout -pubkey
- Using the certificate of the issuer, we can verify server certificate
$ openssl verify -CAfile TERENASSLCA3.crt ocwcspubro.crt
TLS
The Transport Layer Security protocol aims primarily to provide privacy and data integrity between two communicating computer applications. When secured by TLS, connections between a client (e.g., a web browser) and a server (e.g., wikipedia.org) have one or more of the following properties:
- The connection is private because symmetric cryptography is used to encrypt the data transmitted. The keys for this symmetric encryption are based on a shared secret negotiated at the start of the session.
- The identity of the communicating parties can be authenticated using public-key cryptography and digital certificates.
- The connection ensures integrity because each message transmitted includes a message integrity check using a message authentication code.
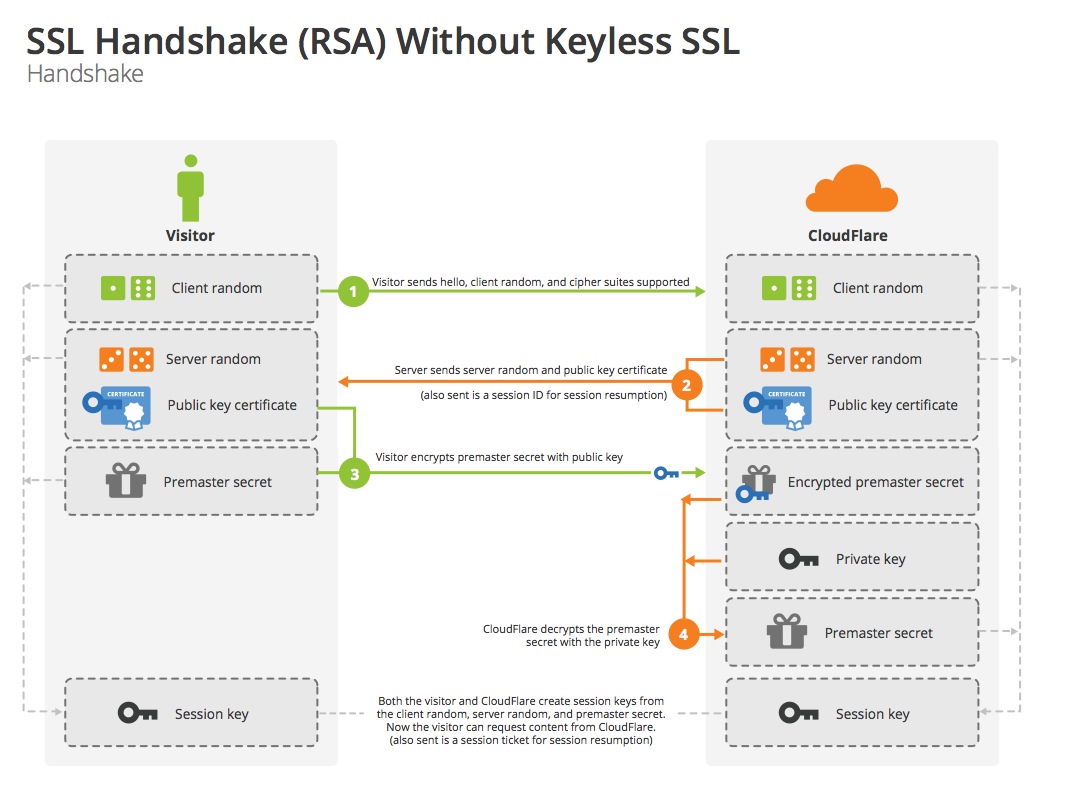
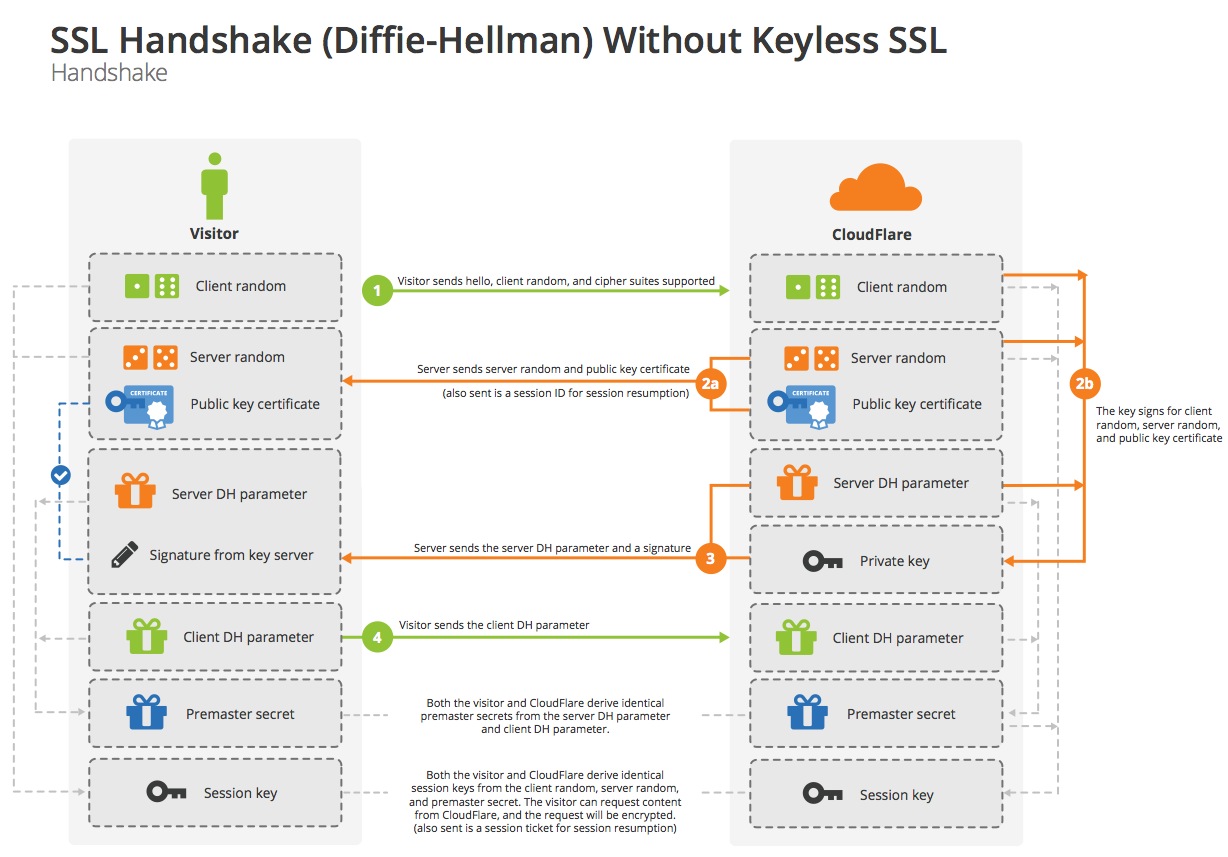
The TLS protocol comprises two layers: the TLS record protocol and the TLS handshake protocol. TLS handshake protocol (both RSA key exchange and Diffie-Hellman key exchange) can be seen in the pictures below:
Task 3: Investigate the TLS handshake protocol
Using Wireshark, investigate the two traffic captures (traffic-captures.tar). In both cases try to find:
- How many ciphersuite does the client support?
- What could be the purpose of Extension: server_name?
- What were the negotiated algorithms?
- What information is sent in cleartext? It is critical? How would a downgrade attack be performed?