Table of Contents
Laboratorul 10 - Analiza Performantei Programelor
The purpose of this lab is the familiarization with the field of application profiling & debugging, through the means of dedicated tools for spotting performance bottlenecks.
We will focus on several open source and commercial tools, as follows:
- valgrind / kcachegrind (on own systems & hpslcluster queue)
- perf (on your own systems)
1. Valgrind / KCachegrind
Valgrind is a tool used for memory debugging, memory leak detection and profiling. It is also a generic framework for creating dynamic analysis tools, such as memory checkers [1].
Valgrind is in essence a virtual machine using just-in-time compilation techniques, including dynamic recompilation. It is important to keep in mind that nothing from the original program ever gets run directly on the host processor. Instead, it will translate the input program into a simpler form called Intermediate Representation (IR), which is processor neutral. After this transformation, a tool [2] is called to do whatever transformation of the IR it needs and the resulting IR is then translated back into machine code and ran on the host processor.
The tools available in Valgrind are:
- memcheck. Used to detect memory-management problems and it is aimed at C and C++ programs. All memory reads and writes are checked, and all calls to malloc/new/free/delete are intercepted. Therefore it can detect memory leaks, access to invalid memory, weird initialization values, overflows, etc. Memcheck runs programs about 10-30x slower than normal;
- cachegrind. Used to profile CPU cache. It performs detailed simulation of the I1, D1 and L2 caches in order to pinpoint the sources of cache misses. It identifies the number of cache misses, memory references and instructions executed for each line of source code. Cache grind runs programs about 20-100x slower than normal;
- callgrind. It is an extension to cachegrind and provides all the information that the latter offers, plus extra information regarding call graphs. In order to view the results, a visualization tool called KCachegrind [3] can be used;
- massif. It is a heap profiler and it performs detailed heap profiling by taking regular snapshots of a program's heap and produces a graph showing heap usage over time, including information about which parts of the program are responsible for the most memory allocations. Massif runs programs about 20x slower than normal;
- helgrind and drd. These tools are thread debuggers which find data races in multithreaded programs. They look for memory locations which are accessed by more than one (POSIX) pthread, but for which no consistently used (pthread_mutex_) lock can be found;
- other 3rd party tools can be found here [4].
2. Analysis of the Tachyon raytracing engine
In this section, we will focus on analyzing a software application. We will analyze both a serial and a parallel implementation. The application is called “tachyon” and you can find the source code attached to this lab.
On your own system, before compilation, you must install the X11 dev tools and create a set of symlinks. For Ubuntu 64 bit, we must do the following:
- install dependencies
sudo apt-get install libx11-dev
- create the symlinks:
sudo mkdir /usr/lib64
sudo ln -s /usr/lib/x86_64-linux-gnu/libX11.so /usr/lib64/libX11.so
sudo ln -s /usr/lib/x86_64-linux-gnu/libXext.so /usr/lib64/libXext.so
To compile it, you must extract the archive Tachyon to local disk and run make. You can test the compilation by running in the same directory:
./tachyon_find_hotspots dat/balls.dat
You should see a window like the one below:
To run and observe the functionalities of this tool, follow the following sequence of steps and instructions:
wget -O tachyon_vtune_amp_xe.tgz http://ocw.cs.pub.ro/courses/_media/asc/lab6/tachyon_vtune_amp_xe.tgz gunzip tachyon_vtune_amp_xe.tgz tar -xvf tachyon_vtune_amp_xe.tar cd tachyon make
Using Valgrind on the Tachyon Code
1. Make sure you have Valgrind and KCachegrind installed on the system (or login on the hp-sl.q queue) and the application in the initial state, without any modifications on your system
sudo apt-get update sudo apt-get install valgrind kcachegrind
2. We will use the tool callgrind to get information from the running application. Run the following command line:
valgrind --tool=callgrind --collect-jumps=yes --dump-instr=yes --collect-systime=yes -- ./tachyon_find_hotspots dat/balls.dat
3. Open the profile in KCachegrind and click on the Calee Map tab. Also, make sure that the buttons % Relative, Cycle detection and Relative to parent are selected. You should see something like this:
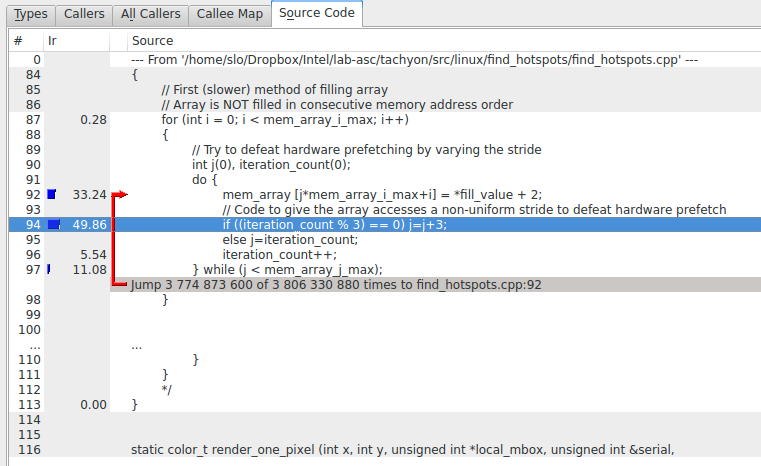
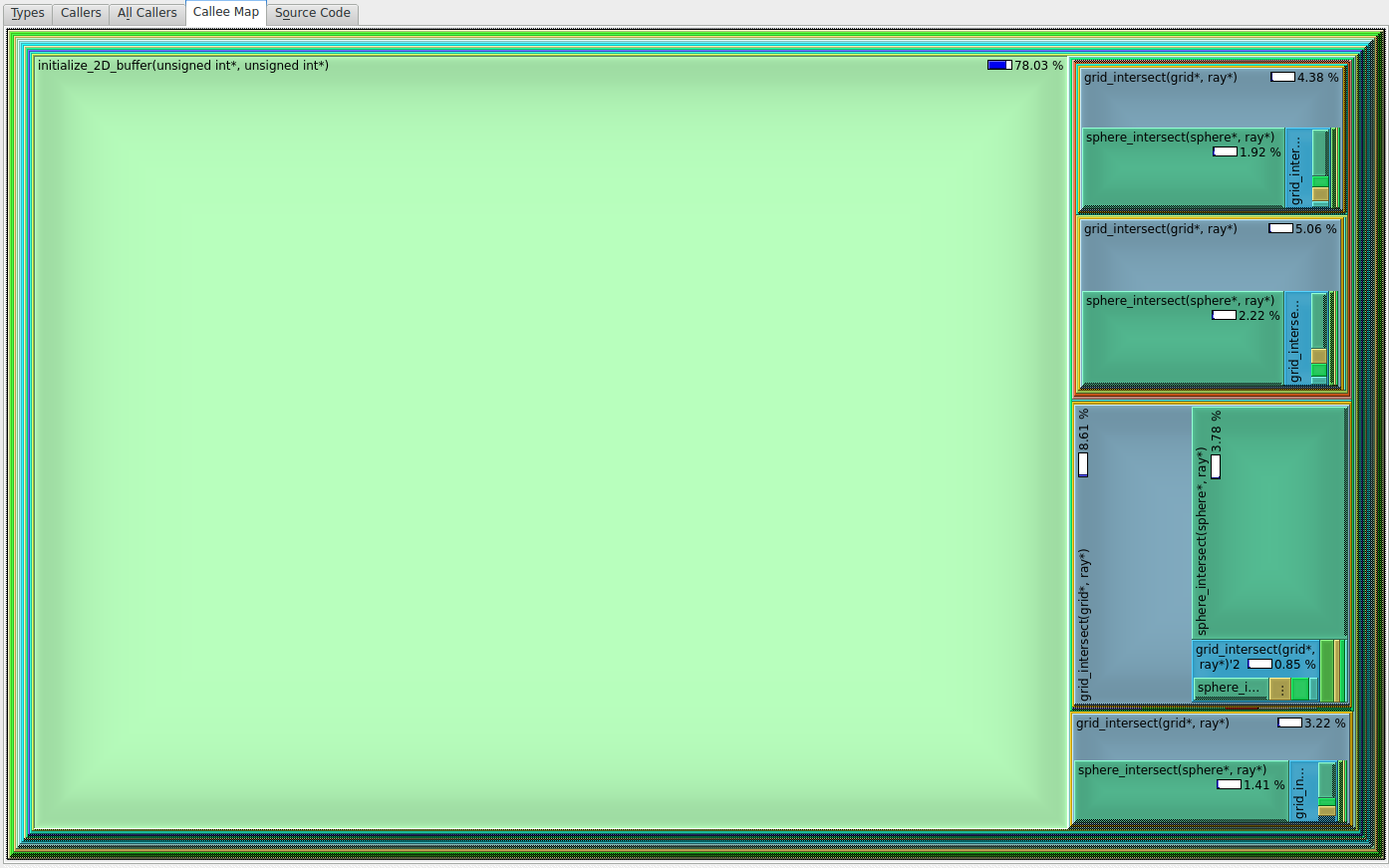 From this image, we can see that valgrind measured that about 78% of the total time was spent in the initialize_2D_buffer function. Double click the square containing the function name, then select the “Source code” tab and you will see the problematic code.
From this image, we can see that valgrind measured that about 78% of the total time was spent in the initialize_2D_buffer function. Double click the square containing the function name, then select the “Source code” tab and you will see the problematic code.
3. Perf
Perf is a performance analysis tool, available in the Linux kernel since version 2.6.31 [5]. The userspace control application is accessed from the command line and provides a number of subcommands. Unlike Valgrind, perf is capable of statistical profiling of both the entire system (kernel and userspace) and per process PID basis. It supports hardware performance counters, tracepoints, software performance counters (e.g. hrtimer), and dynamic probes (for example, kprobes or uprobes).
Perf is used with several subcommands:
- stat: measure total event count for a single program or for the whole system for a specified time period;
- top: top-like dynamic view of hottest functions;
- record: measure and save sampling data for single program;
- report: analyze file generated by perf record;
- annotate: annotate sources or assembly;
- sched: tracing/measuring of scheduler actions and latencies;
- list: list available events.
1. Make sure you have perf installed on the system and the application in the initial state, without any modifications. You can only run perf as root. You can only do this on your system. 2. Run the following command line:
perf record -a -g -- ./tachyon_find_hotspots
For other perf parameters, you can read this link 3. Run the following command line to view the collected results:
perf report
You should see a screen like the following:
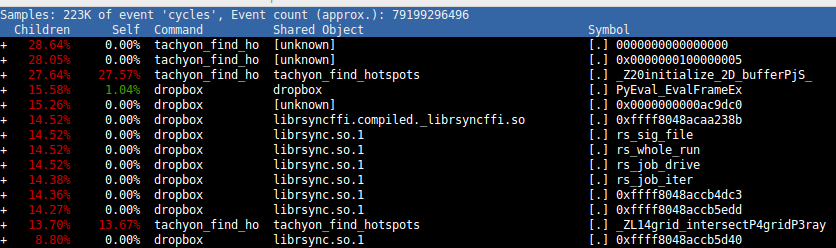 From this image you can see that perf will display the symbol for the function that takes the most amount of CPU time in red. In our case it’s the _Z20initialize_2D_bufferPjS_, which translates in the C source code into the same function as with VTune and Valgrind.
From this image you can see that perf will display the symbol for the function that takes the most amount of CPU time in red. In our case it’s the _Z20initialize_2D_bufferPjS_, which translates in the C source code into the same function as with VTune and Valgrind.
c++filt _Z20initialize_2D_bufferPjS_
Exercitii
Pentru acest laborator se pot utiliza sistemele din cluster prin intermediul fep.grid.pub.ro:
ssh -Y username@fep.grid.pub.ro(natural puneti utilizatorul vostru in loc de username)wget https://ocw.cs.pub.ro/courses/_media/asc/lab6/lab6_skl.tar.gz -O lab6_skl.tar.gz- Downloadati arhiva laboratoruluitar -xzvf lab6_skl.tar.gz- dezarhivati arhiva downloadata mai sussrun --time 00:05:00 --x11 -p haswell --pty /bin/bash- conectati-va pe coada Haswell cu 14 servereapptainer run docker://gitlab.cs.pub.ro:5050/asc/asc-public/c-labs:1.3.1 /bin/bash- accesati imaginea de docker in cadrul căreia avem permisiunile necesare realizării laboratorului
Task 0 - Folosit valgrind pentru task0.c urmarind TODO-uri pentru teste.
make task0pentru versiunea serialamake openmp_task0pentru versiunea paralelizata[@fep ]$ srun --time 00:05:00 --x11 -p haswell --pty /bin/bash [@haswell-wnxx ~]$ apptainer run docker://gitlab.cs.pub.ro:5050/asc/asc-public/c-labs:1.3.1 /bin/bash Apptainer> make task0 Apptainer> valgrind --tool=callgrind -v --dump-every-bb=10000000 ./task0 Apptainer> kcachegrind Apptainer> make clean Apptainer> make openmp_task0 Apptainer> valgrind --tool=callgrind -v --dump-every-bb=10000000 ./task0 Apptainer> kcachegrind
Task 1 - Analizati aplicatia Tachyon.
- Rulati scriptul
task1.shpentru a descarca si compila Tachyon. Atentie, trebuie sa rulati pe fep scriptul task1.sh pentru ca doar aici aveti disponibil libX11.so de care aveti nevoie pentru compilare. Pe masinile proprii aveti de asemenea nevoie de libX11.so asa incat e bine sa il intalati inainte de rularea acestui task. - Varianta seriala
tachyon_find_hotspots - Varianta paralelizata
tachyon_analyze_locks [@fep ~]$ ./task1.sh [@fep ]$ srun --time 00:05:00 --x11 -p haswell --pty /bin/bash [@haswell-wn01 ~]$ apptainer run docker://gitlab.cs.pub.ro:5050/asc/asc-public/c-labs:1.3.1 /bin/bash Apptainer> cd tachyon Apptainer> valgrind --tool=callgrind --collect-jumps=yes --dump-instr=yes --collect-systime=yes -- ./tachyon_find_hotspots dat/balls.dat Apptainer> valgrind --tool=callgrind --collect-jumps=yes --dump-instr=yes --collect-systime=yes -- ./tachyon_analyze_locks dat/balls.dat
- Analizati cu perf
Task 2 - Folositi tool-ul cachegrind din valgrind pentru a analiza codul care realizeaza inmultirea de matrice folosind diferite reordonari ale buclelor.
- Compilati si rulati
task2.c - Notati observatiile voastre legate de numarul de I refs, D refs, D1 misses, branches si mispredicts.
[@fep ]$ srun --time 00:05:00 --x11 -p haswell --pty /bin/bash [@haswell-wn01 ~]$ apptainer run docker://gitlab.cs.pub.ro:5050/asc/asc-public/c-labs:1.3.1 /bin/bash Apptainer> make task2 Apptainer> valgrind --tool=cachegrind --branch-sim=yes ./task2 1 Apptainer> valgrind --tool=cachegrind --branch-sim=yes ./task2 2 Apptainer> valgrind --tool=cachegrind --branch-sim=yes ./task2 3
exit
Alternativ, daca ati uitat sesiuni deschise, puteti verifica acest lucru de pe fep.grid.pub.ro, utilizand comanda squeue. In cazul in care identificati astfel de sesiuni “agatate”, le puteti sterge (si va rugam sa faceti asta), utilizand comanda scancel ID unde ID-ul il identificati din comanda anterioara squeue. Puteți folosi mai precis squeue -u username (username de pe fep.grid.pub.ro) pentru a vedea doar sesiunile care vă interesează.
Daca nu veti face aceasta delogare, veti putea ajunge in situatia in care sa nu va mai puteti loga pe nodurile din cluster.
Reference
Resources
- Responsabilii acestui laborator: Emil Slusanschi, Alexandru Patrascu si Octavian Moraru.